It all starts with <Connect />
Configure your <Connect /> component with the connector of your choice and the operations scope you’ll need to build your integration.
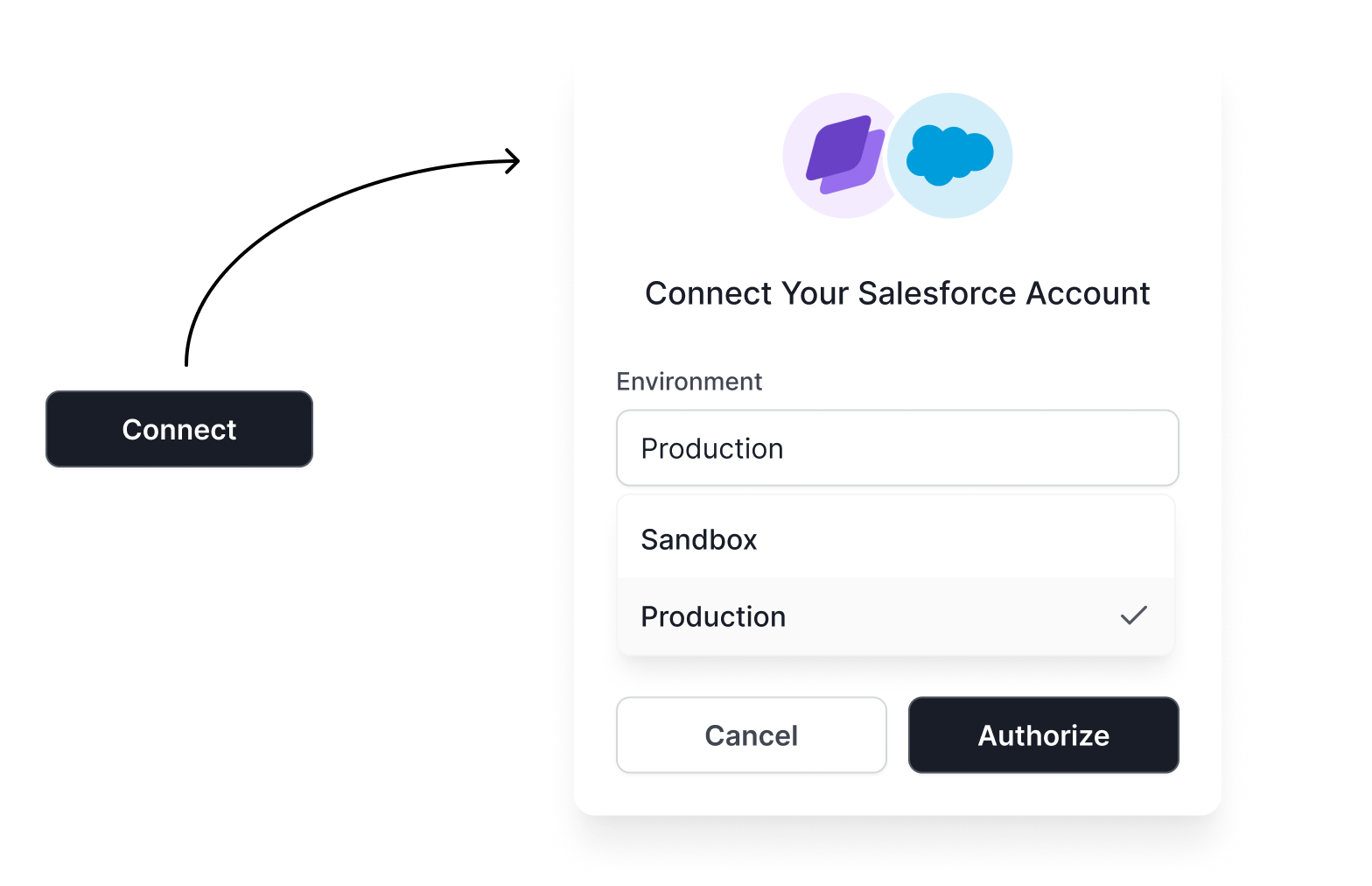
Live Demo
Select a connector below to experience our seamless authentication flow and see how easy it is to connect third-party services.
Select a connector below to experience our seamless authentication flow and see how easy it is to connect third-party services.
SSR component
Server
Next
Models
List, create, update seamlessly
contact, opportunity, ticket and over
30 other unified model across all connectors,
simplifying your integrations with a single codebase.Bi-direction Synchronization
Real-time bidirectional data synchronization between any connector’s model
(e.g
contact) and your own database.Security & Compliance
- All credentials are encrypted at rest
- Follows OAuth 2.0 best practices
- Compliant with security standards